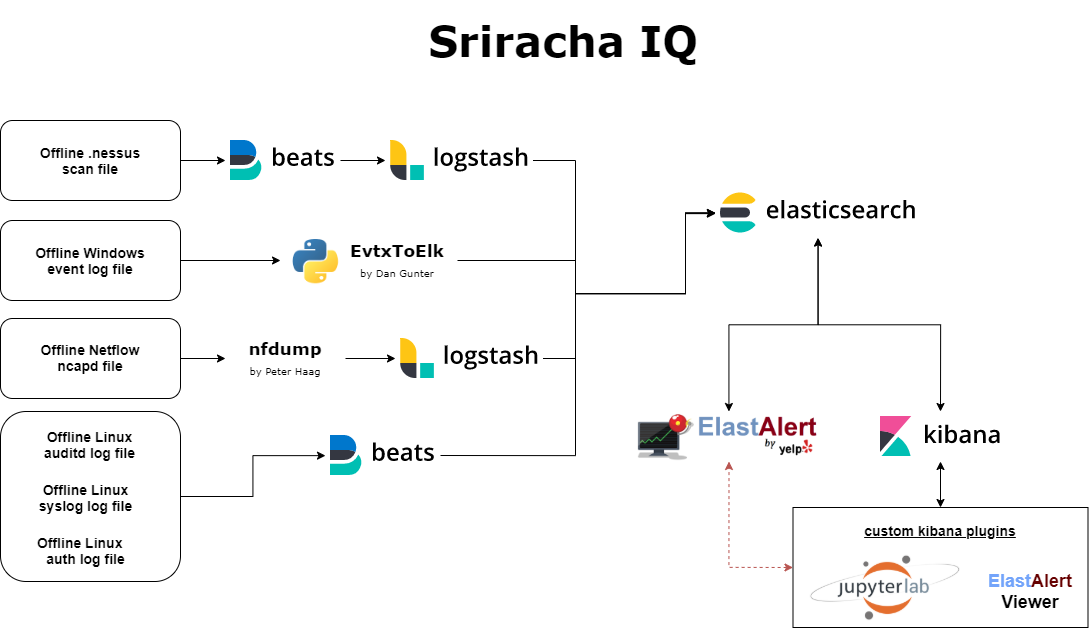
Amazon.com: Threat Hunting with Elastic Stack: Solve complex security challenges with integrated prevention, detection, and response eBook : Pease, Andrew: Kindle Store
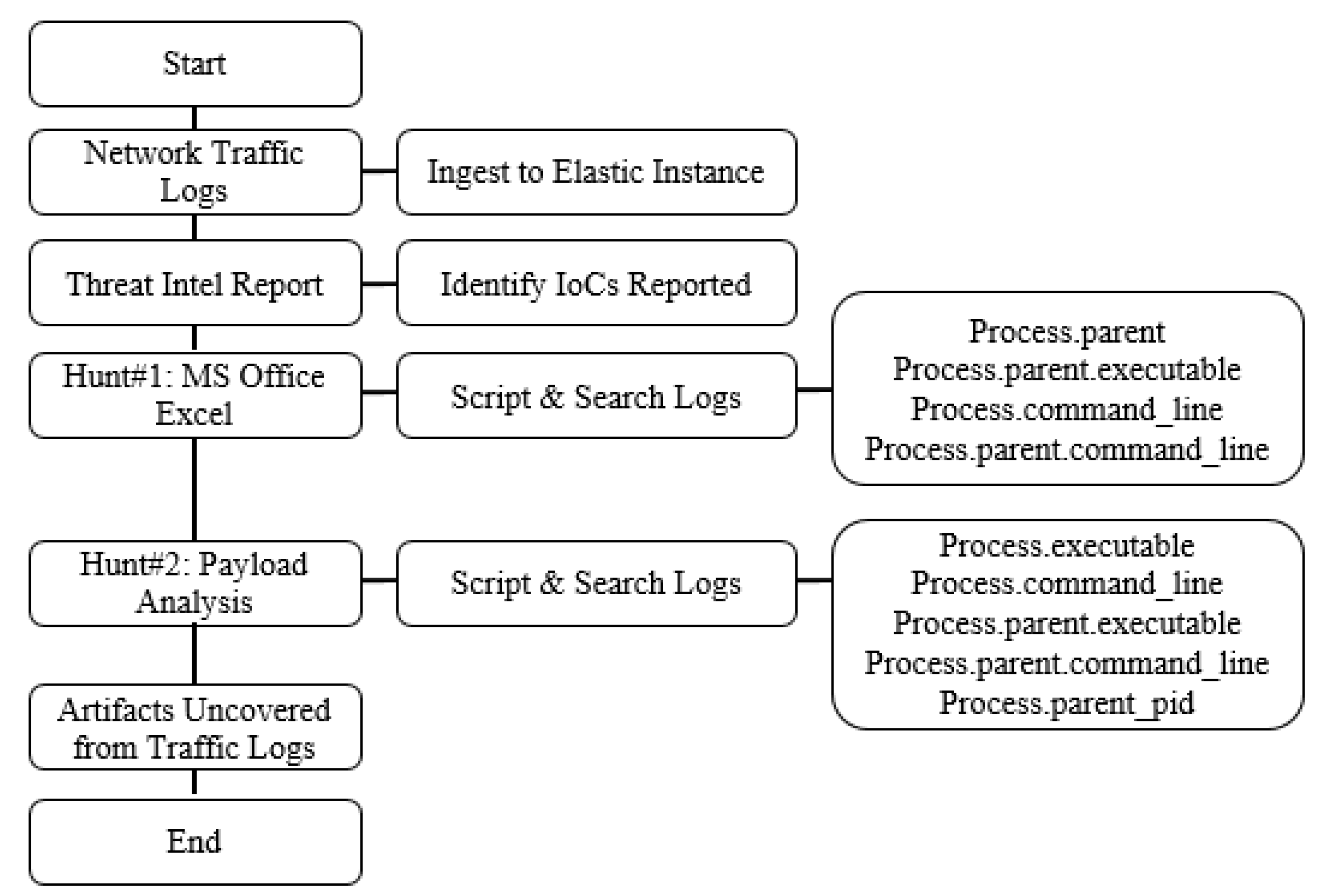
Electronics | Free Full-Text | BTH: Behavior-Based Structured Threat Hunting Framework to Analyze and Detect Advanced Adversaries

Threat Hunting with Elastic Stack: Solve complex security challenges with integrated prevention, detection, and response: 9781801073783: Computer Science Books @ Amazon.com

Threat Hunting with Elastic Stack: Solve complex security challenges with integrated prevention, detection, and response: 9781801073783: Computer Science Books @ Amazon.com

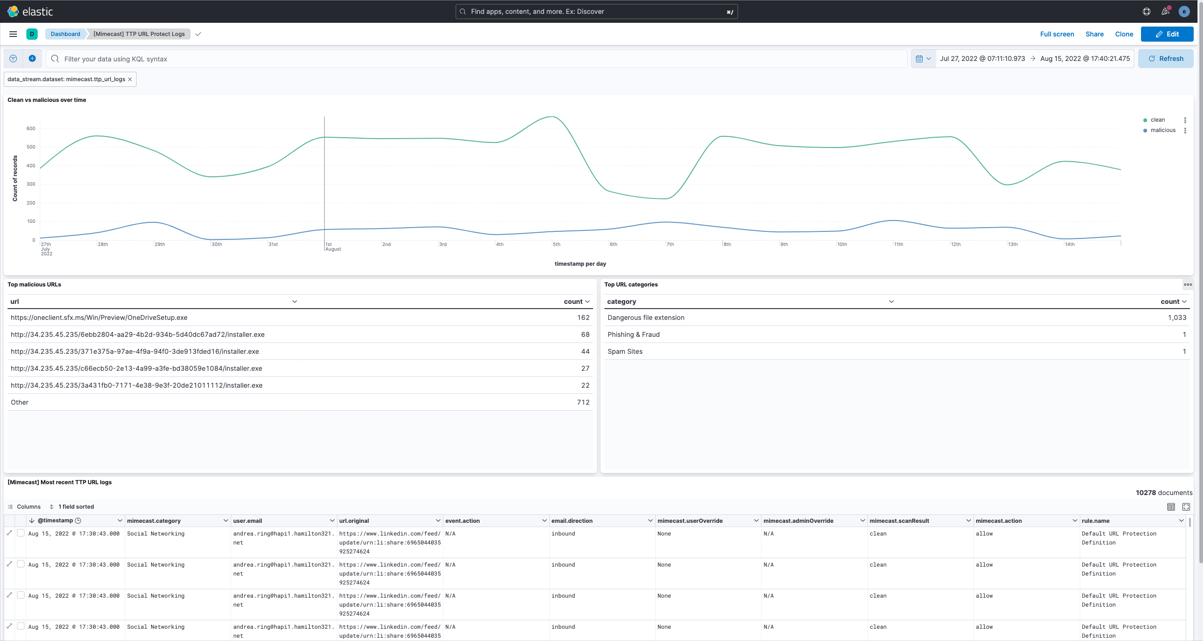
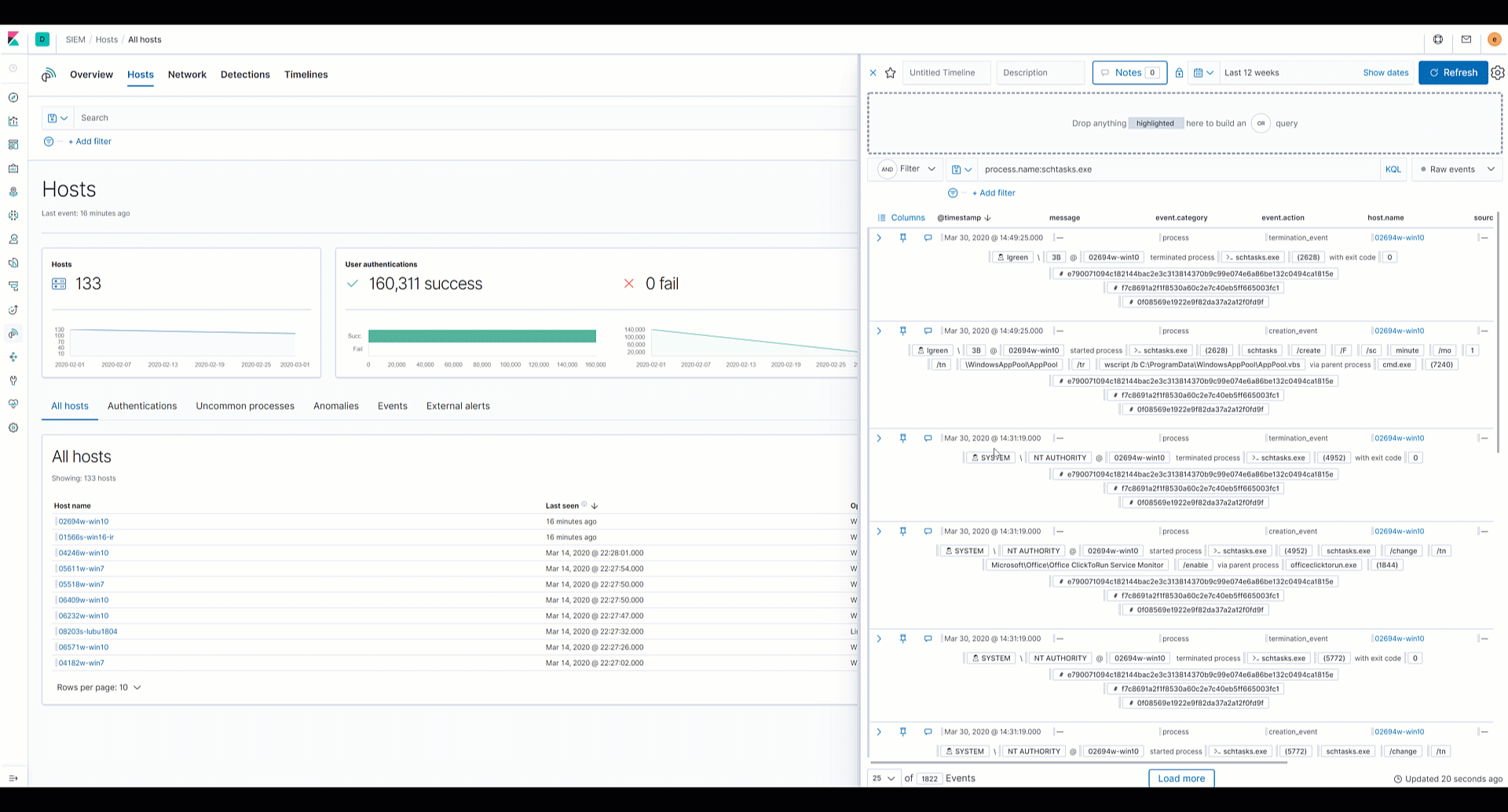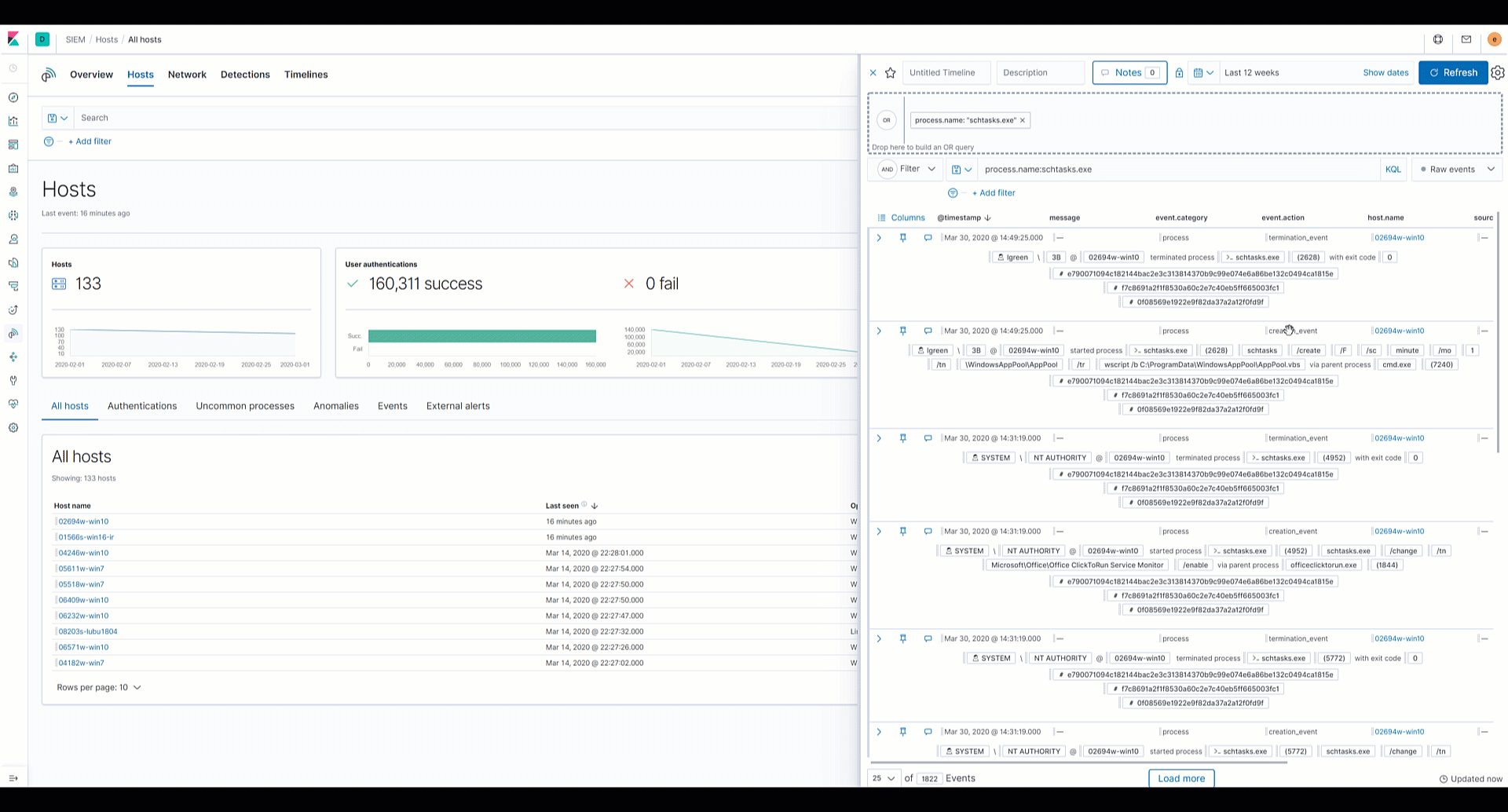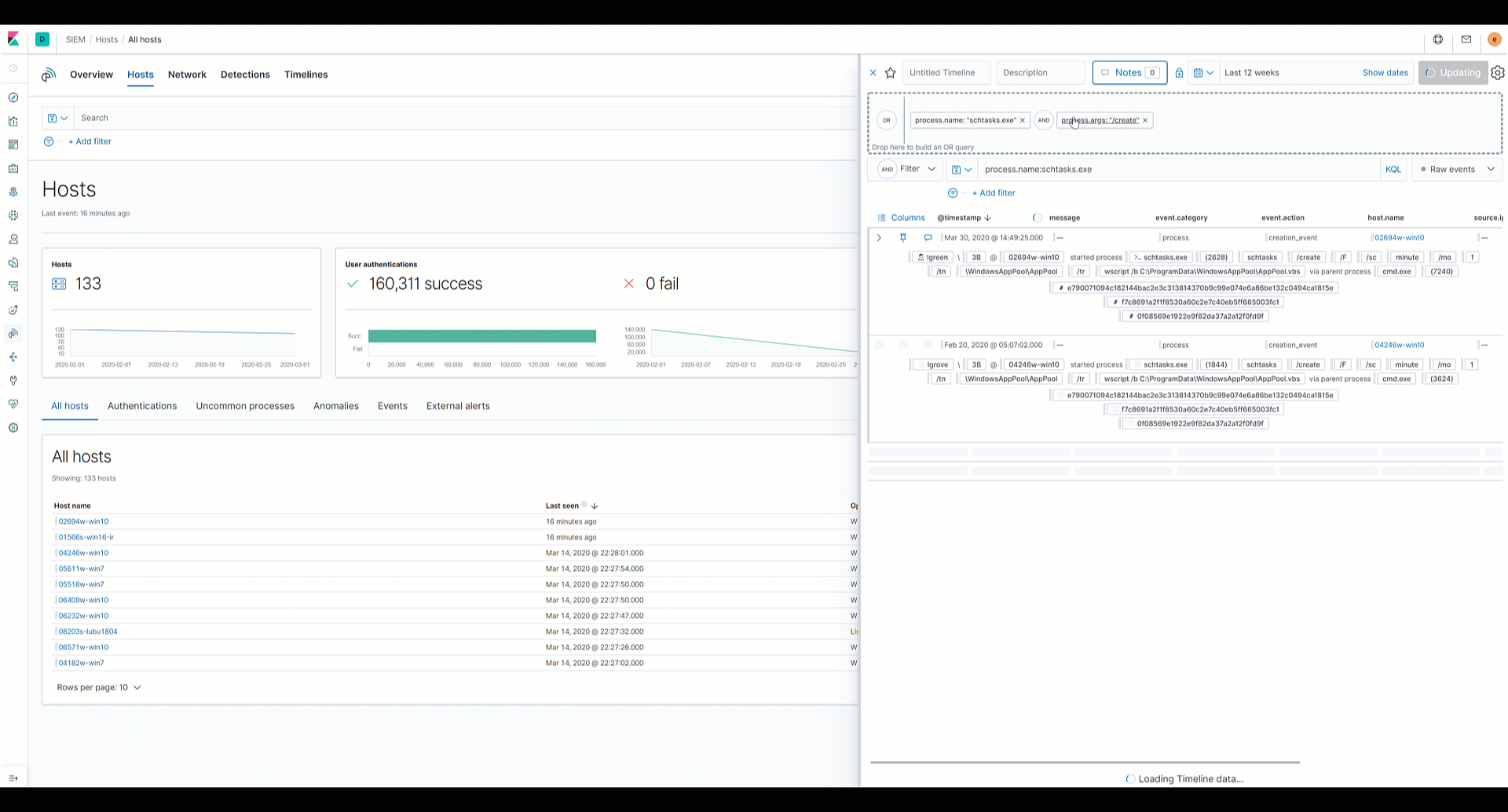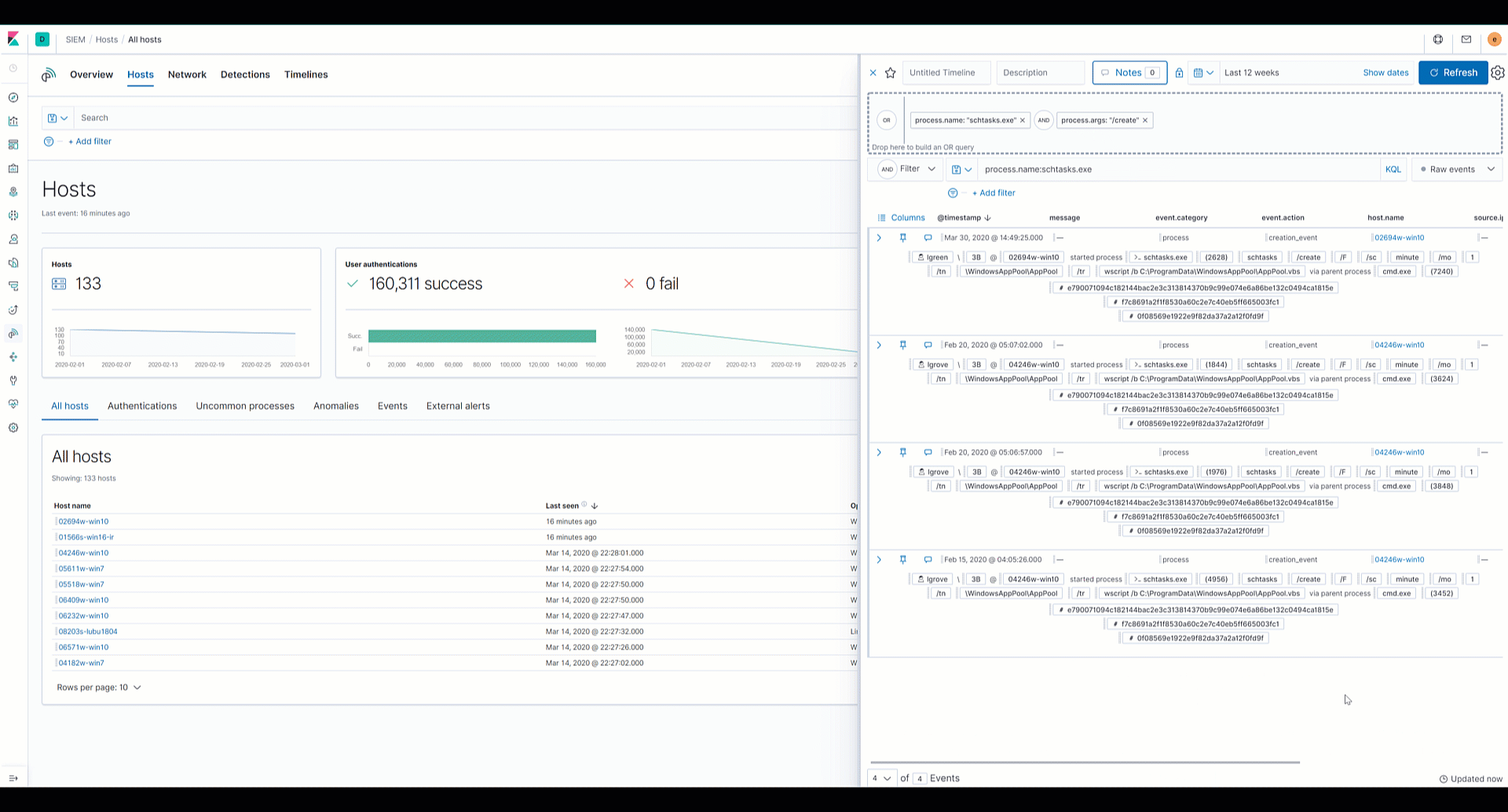
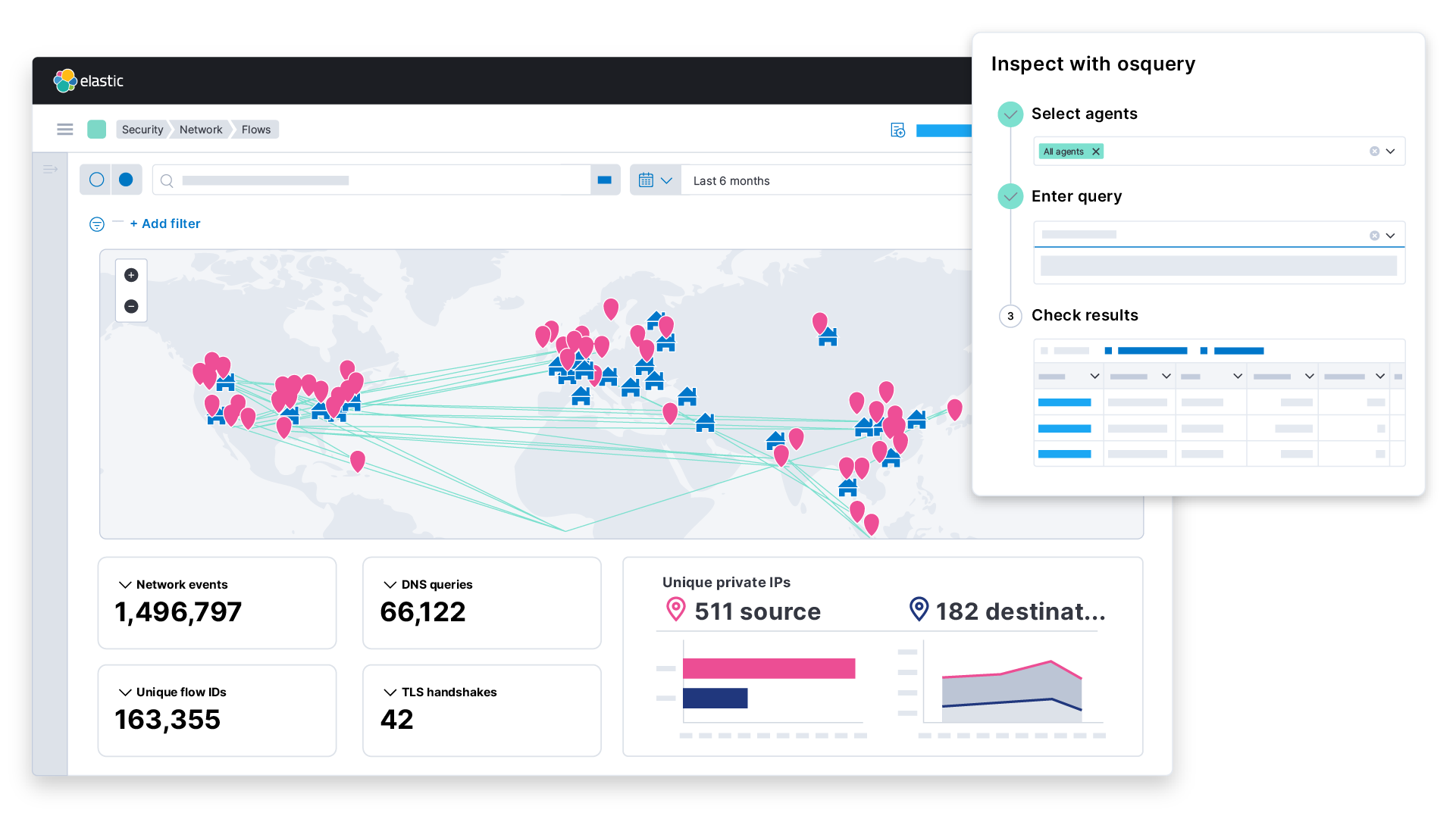
Elastic SIEM: Speed, scale, and analytical power drive your security operations and threat hunting - Help Net Security
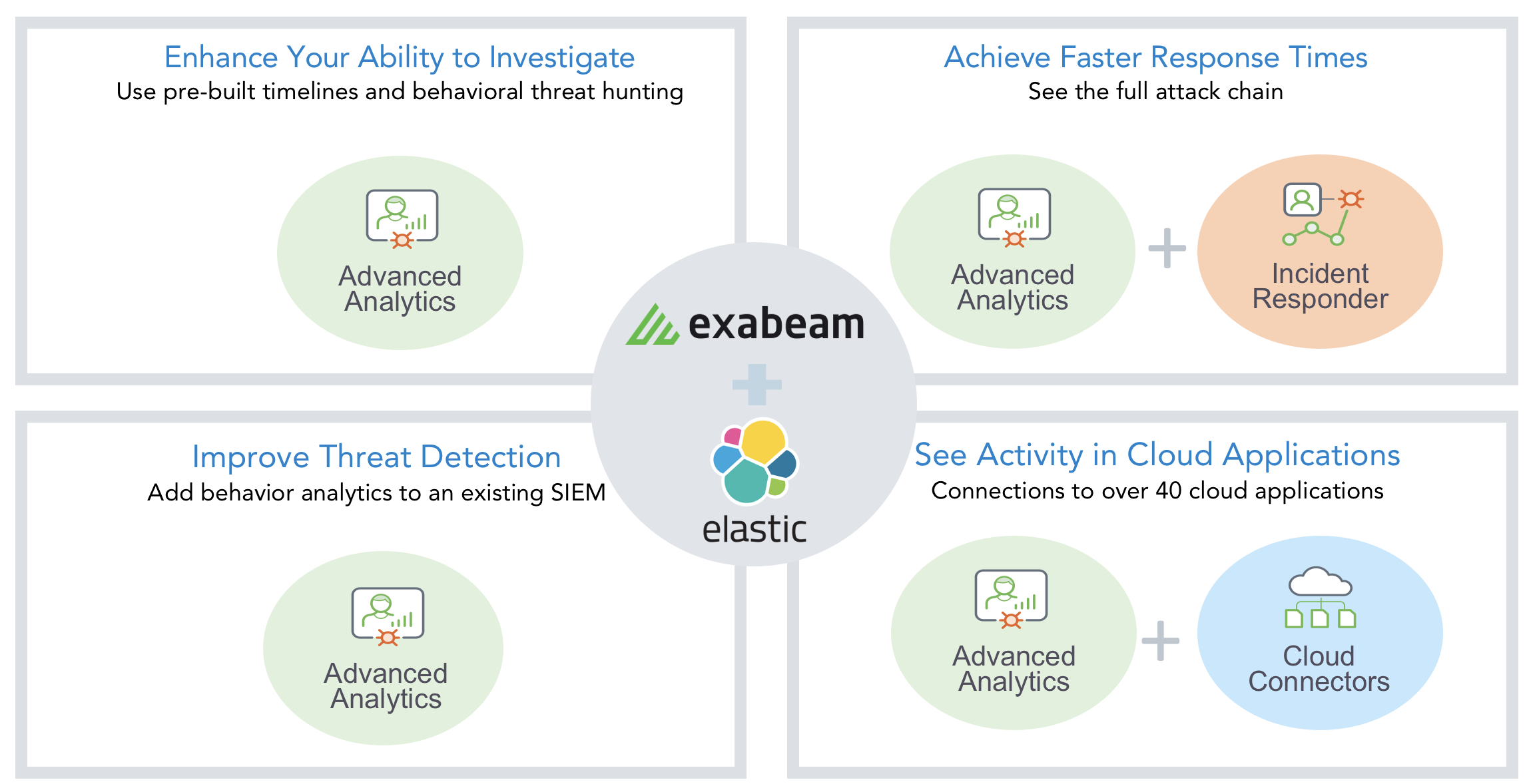
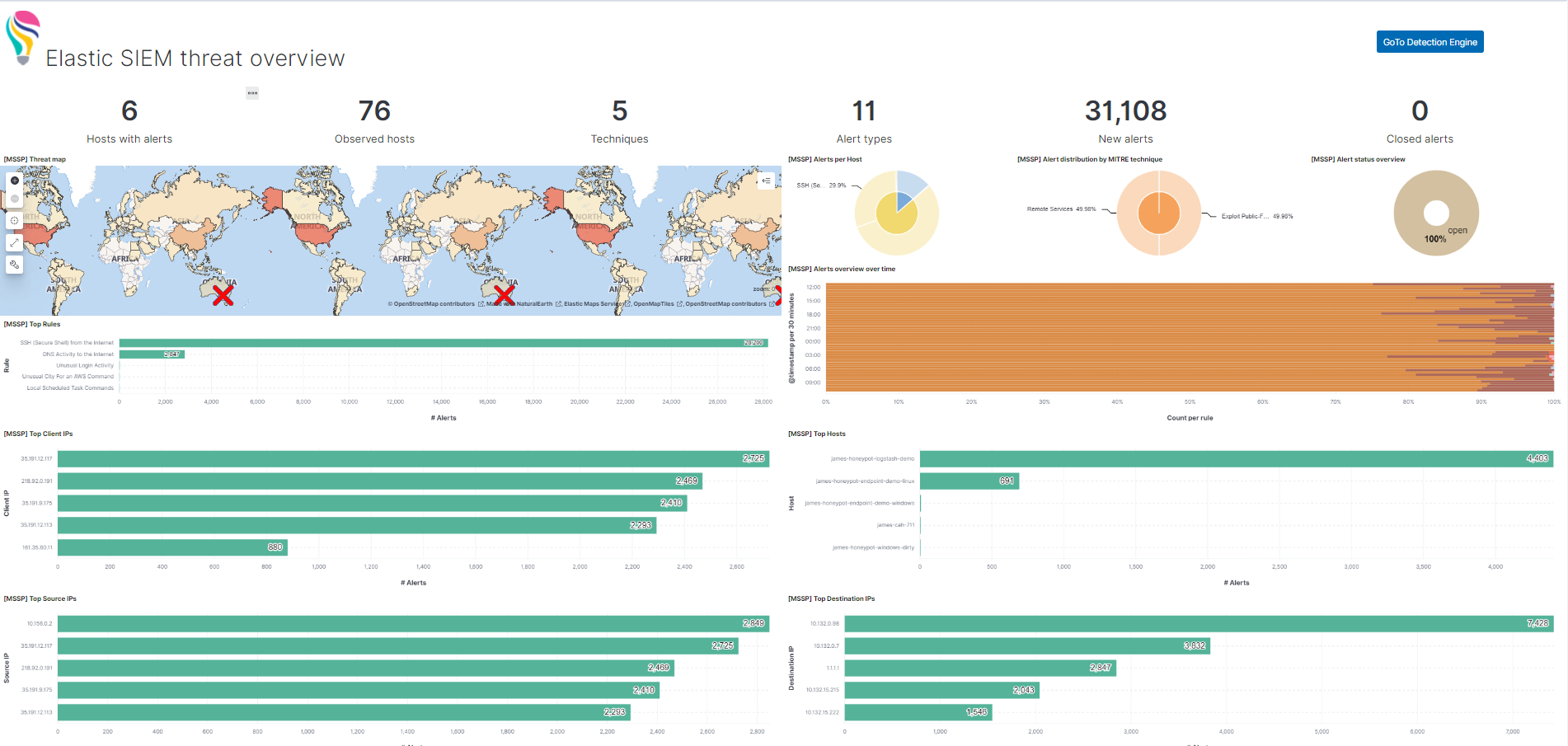
Improve Threat Detection, Enhance Ability to Investigate, Reduce Incident Response Times and Enhance Cloud Security on Elastic SIEM with Exabeam