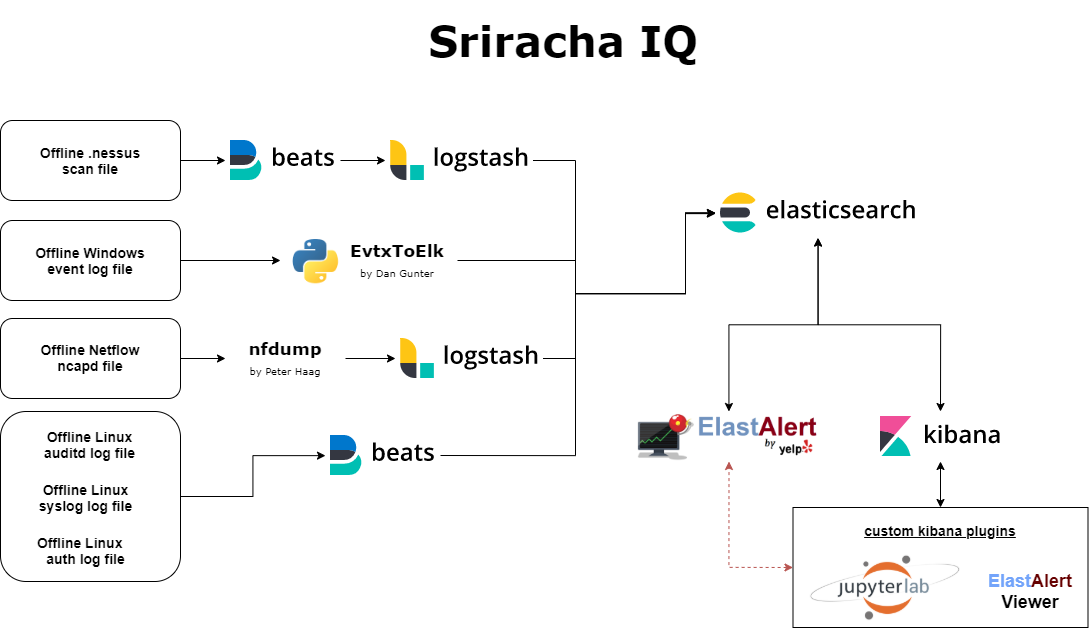
GitHub - tiburon-security/sriracha-iq: Rapid cybersecurity toolkit based on Elastic in Docker. Designed to quickly build elastic-based environments to analyze and execute threat hunting, blue team assessments, audits, and security control assessments.

Axelle Decottignies sur LinkedIn : Elastic's 2022 Global Threat Report: A roadmap for navigating today's…

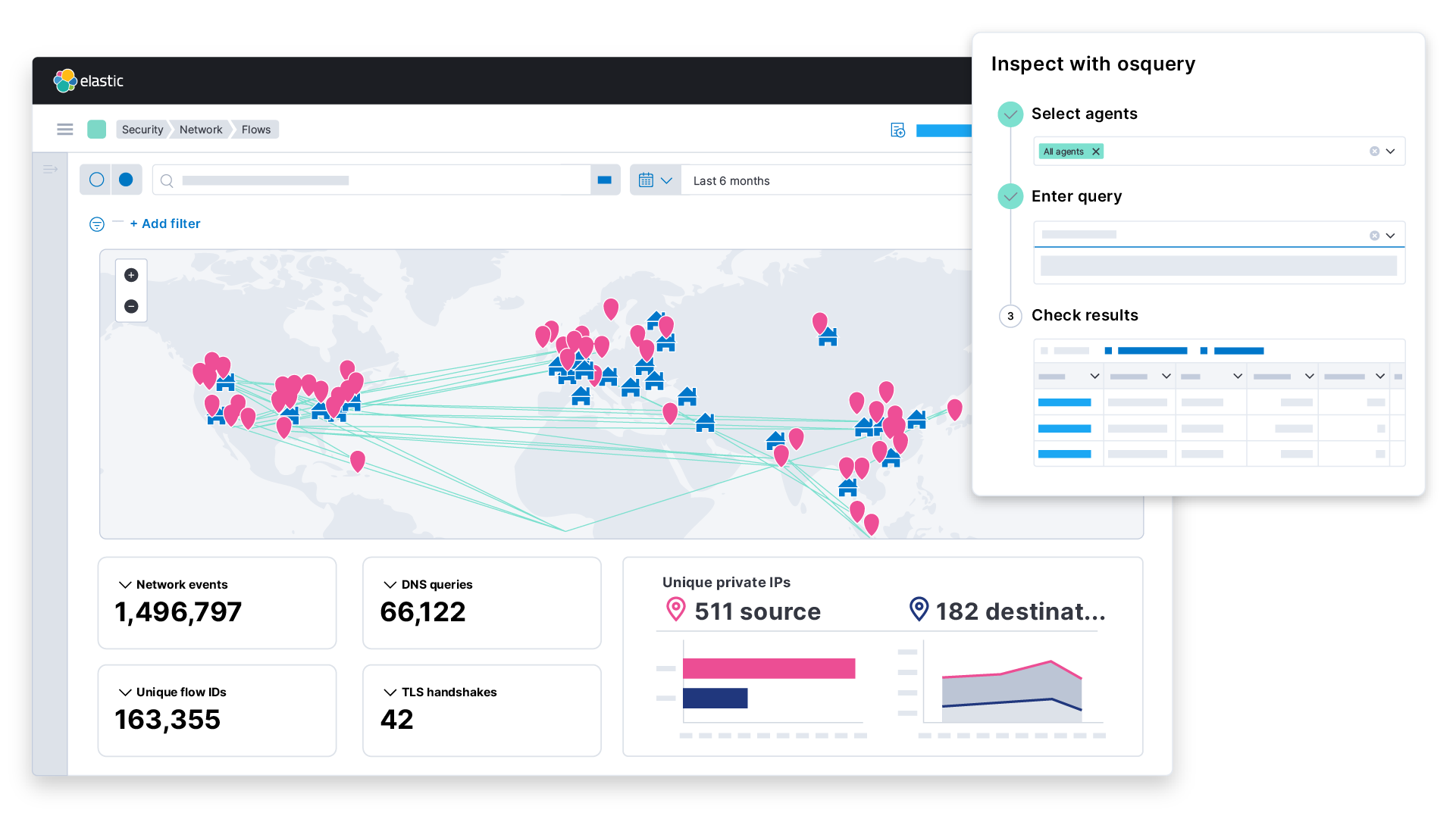


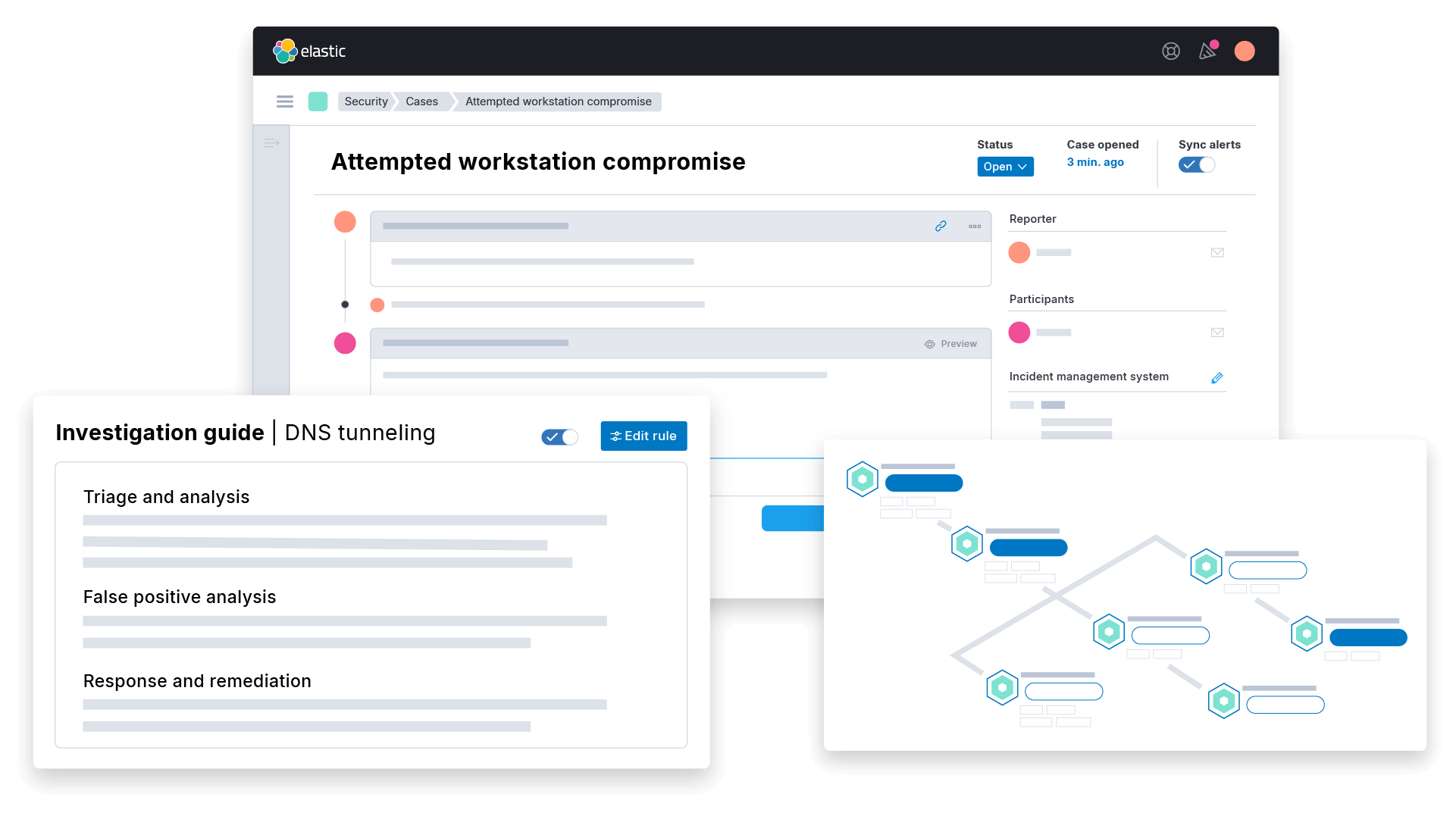



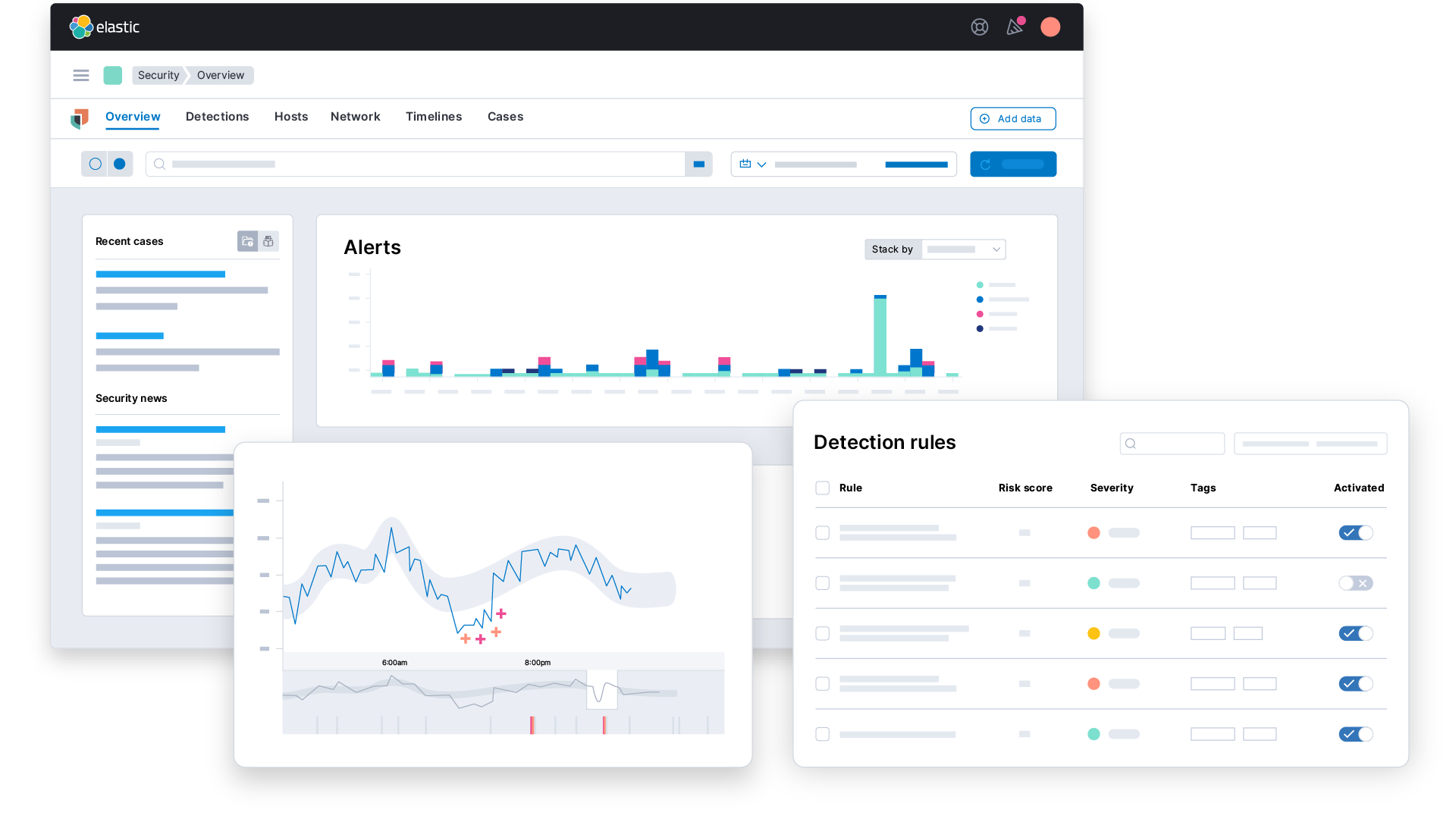
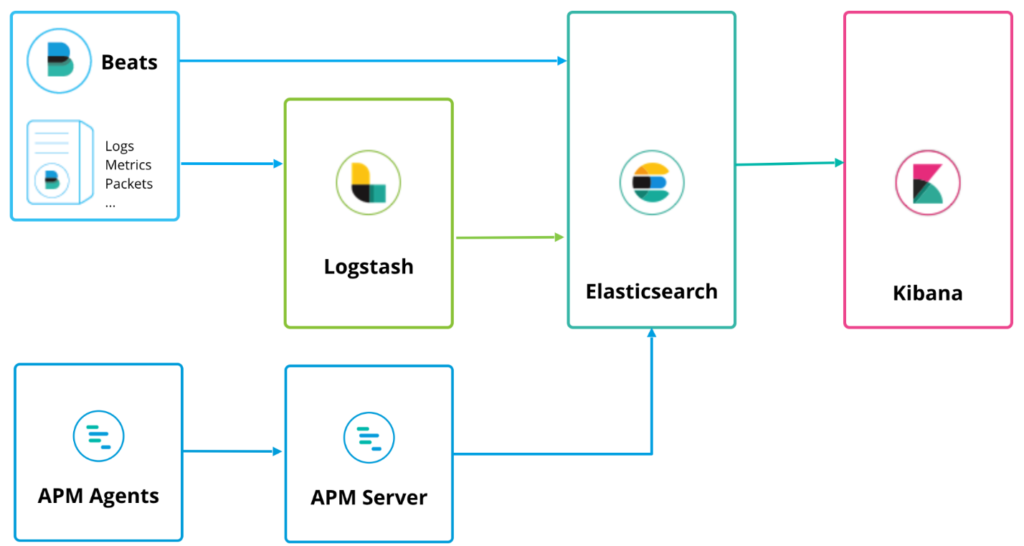






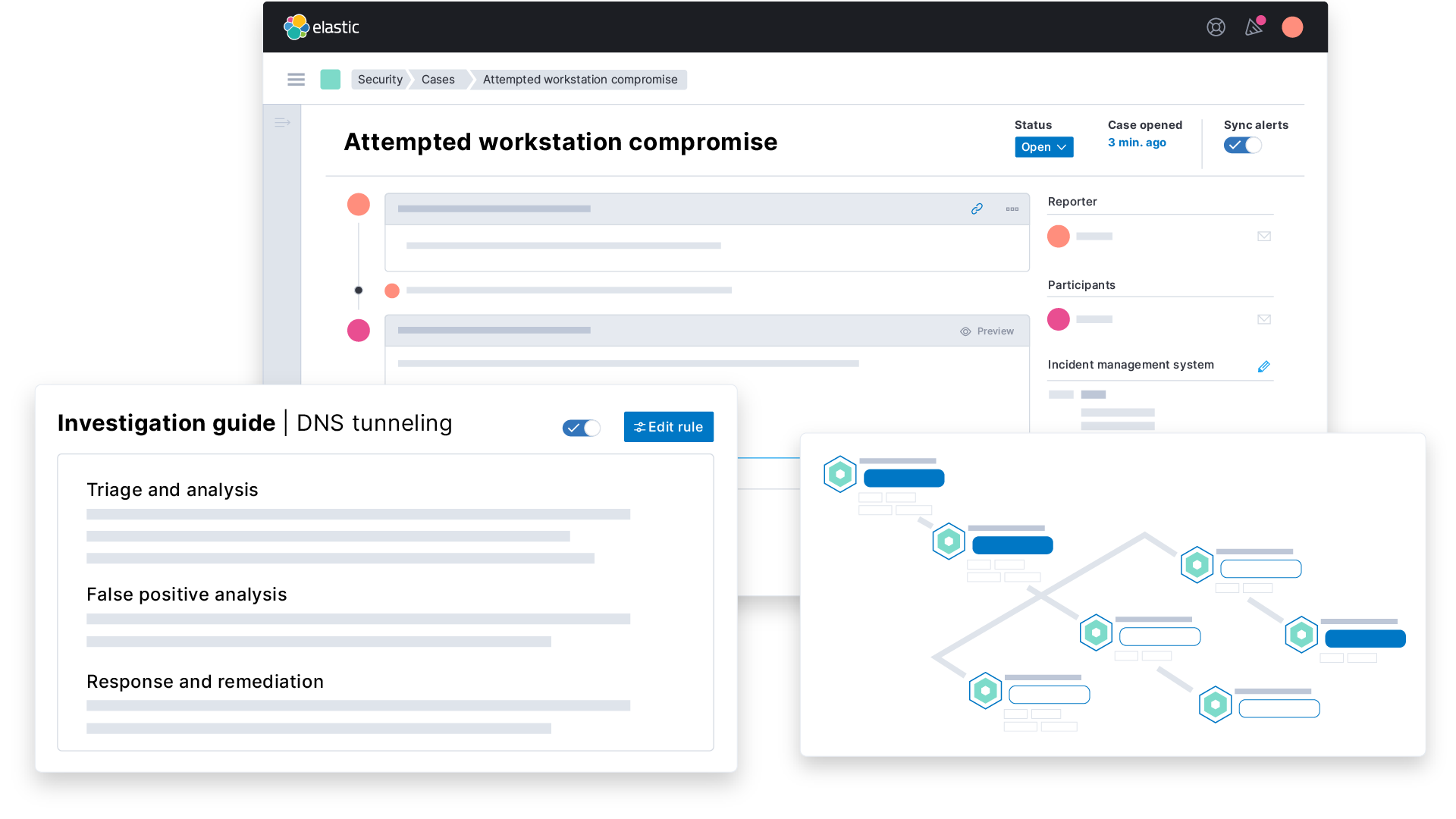

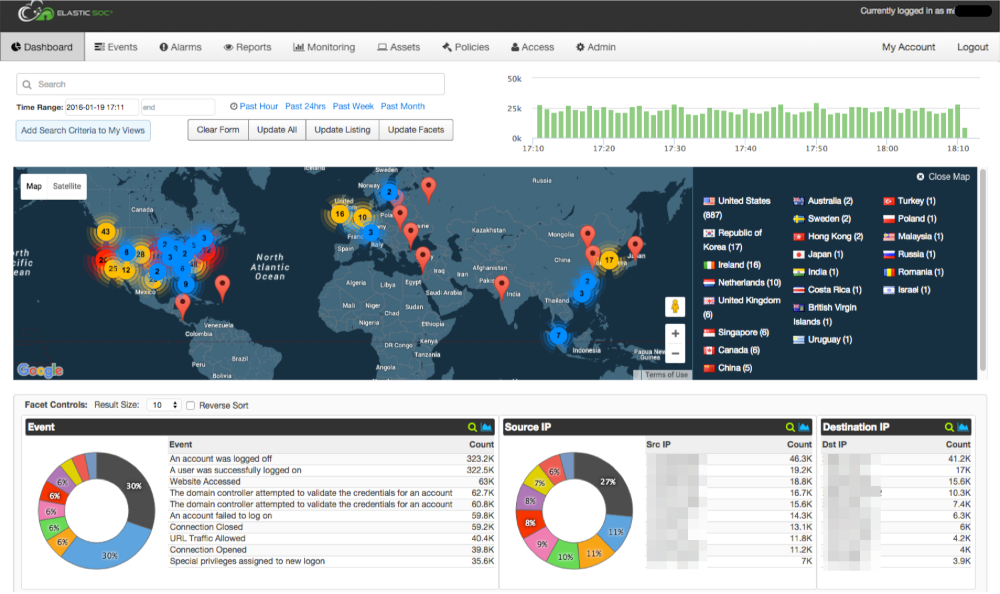
![Configure security for the Elastic Stack | Elasticsearch Guide [7.17] | Elastic Configure security for the Elastic Stack | Elasticsearch Guide [7.17] | Elastic](https://www.elastic.co/guide/en/elasticsearch/reference/7.17/images/elastic-security-overview.png)


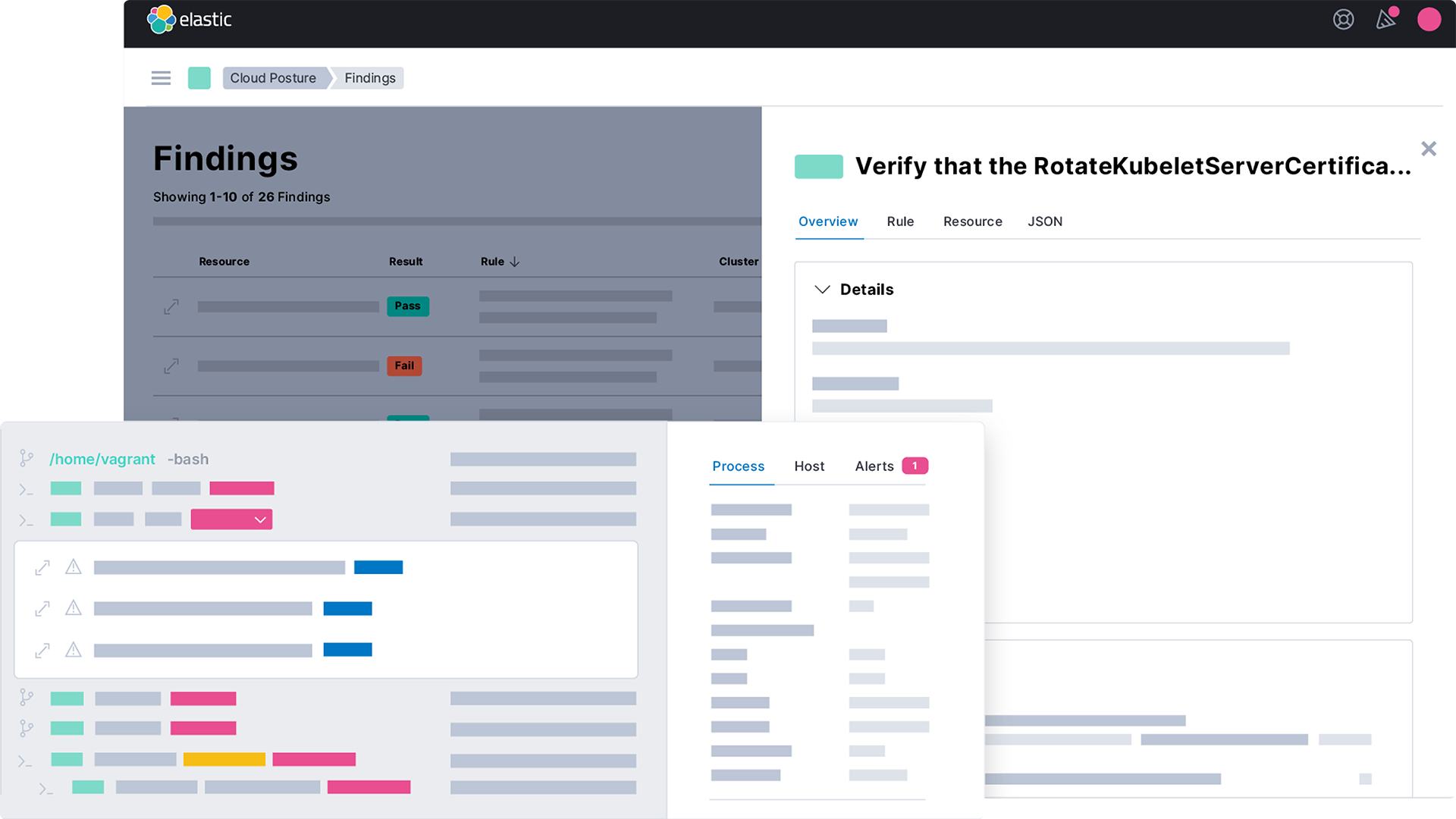
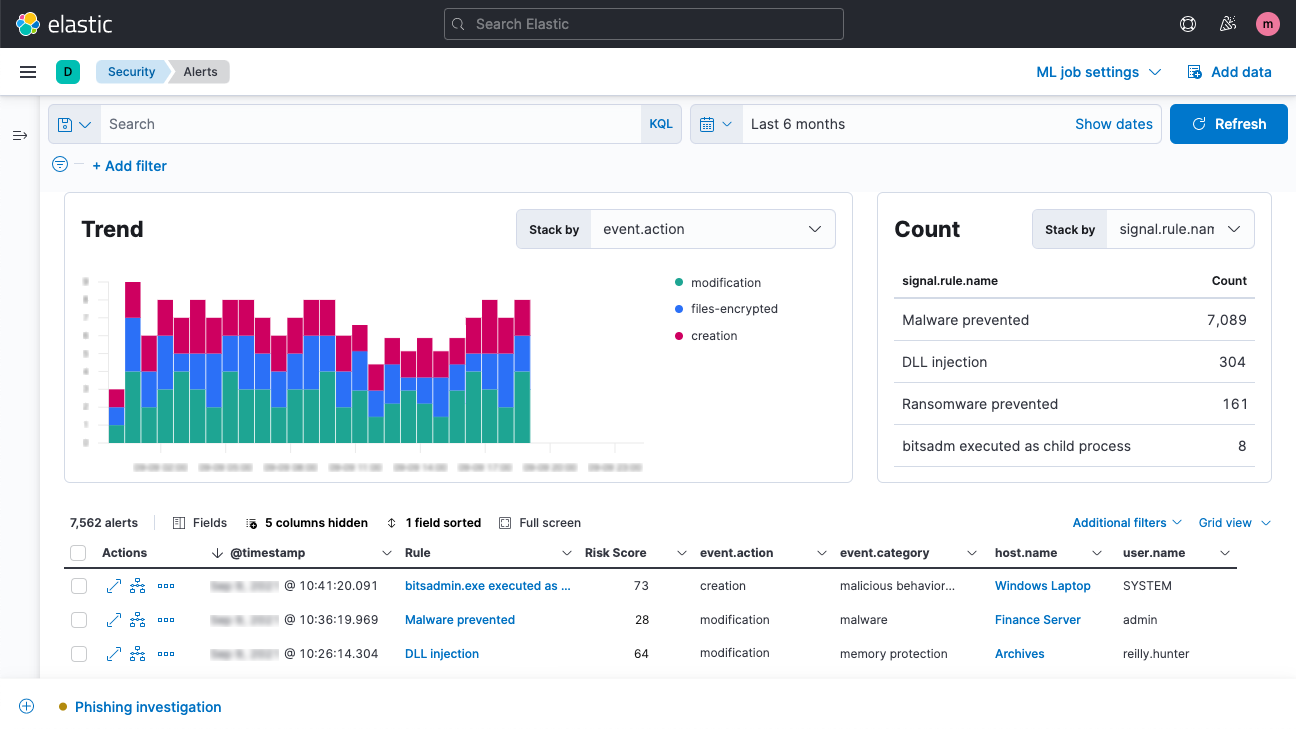
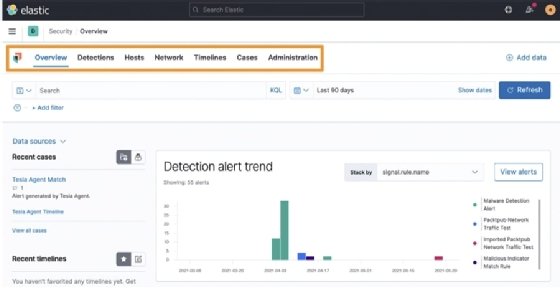
![Detections and alerts | Elastic Security Solution [8.12] | Elastic Detections and alerts | Elastic Security Solution [8.12] | Elastic](https://www.elastic.co/guide/en/security/current/images/alert-page.png)